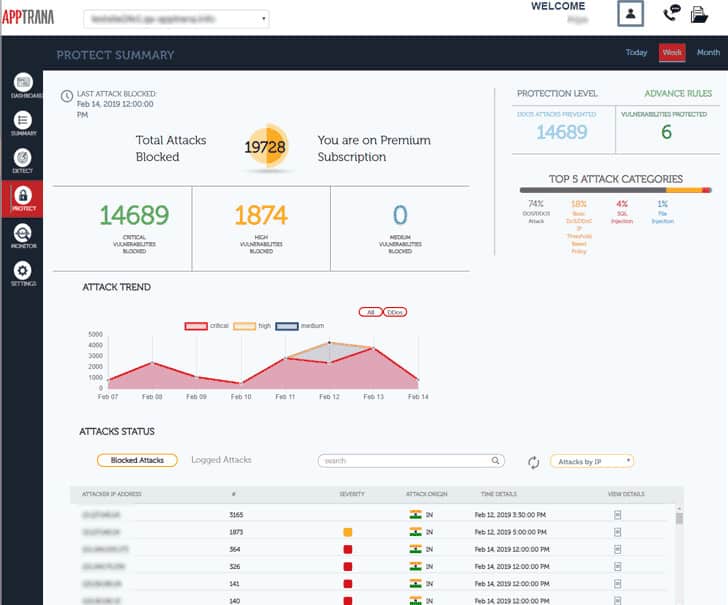
2018 DDoS Attack Landscape-7 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

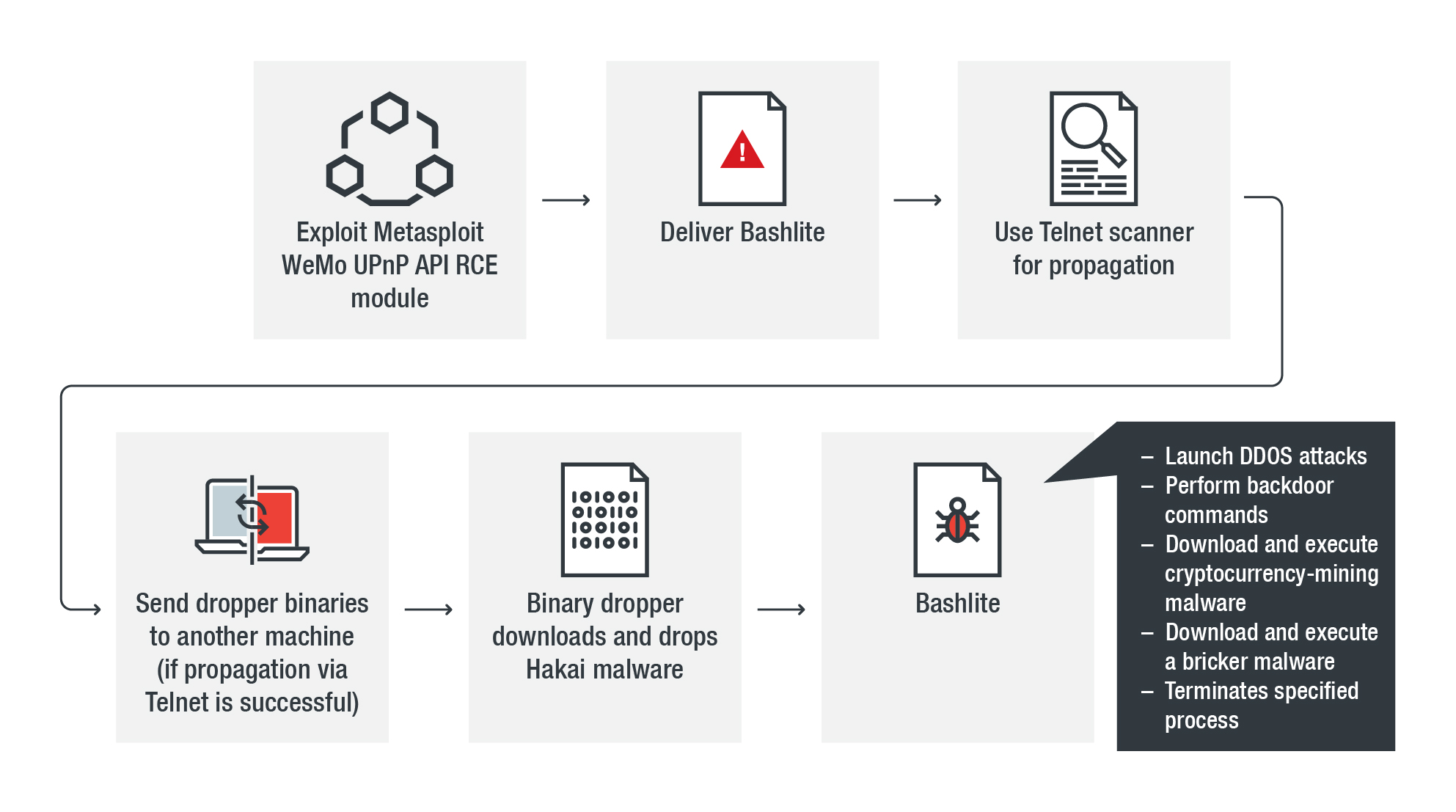
Observations from a Log4j Decoy: From Vulnerability to Infection to DDOS in Record Time - Fidelis Cybersecurity