![Cyber Report [Jun 08, 22] Building the Right Cyber Workforce; Deep Dive on SBOMs & HBOMs - Defense & Aerospace Report Cyber Report [Jun 08, 22] Building the Right Cyber Workforce; Deep Dive on SBOMs & HBOMs - Defense & Aerospace Report](https://defaeroreport.com/wp-content/uploads/2022/06/Screen-Shot-2022-06-08-at-12.32.36-PM.png)
Cyber Report [Jun 08, 22] Building the Right Cyber Workforce; Deep Dive on SBOMs & HBOMs - Defense & Aerospace Report

Deep Instinct partners with Integrity360 to deliver end-to-end deep learning cyber security to UK enterprises - EnterpriseTalk
Deep Cybersecurity: A Comprehensive Overview from Neural Network and Deep Learning Perspective | SpringerLink

2022 Cybersecurity Deep Dive: Have Integrators Finally Embraced Cyber? - Security Sales & Integration

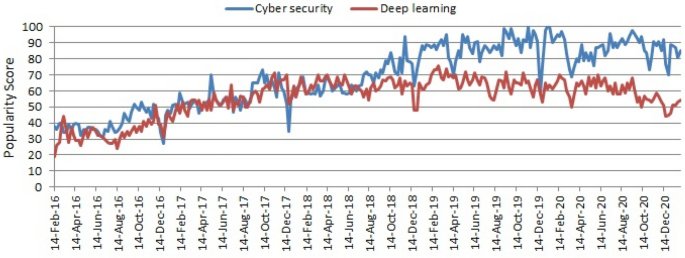
Deep Learning Applications for Cyber-Physical Systems: 9781799881612: Computer Science & IT Books | IGI Global